Clarity Voice VoIP Network
Safe. Secure. Scalable.
Protecting your communications against fraud and abuse.
Security – why do I need it?
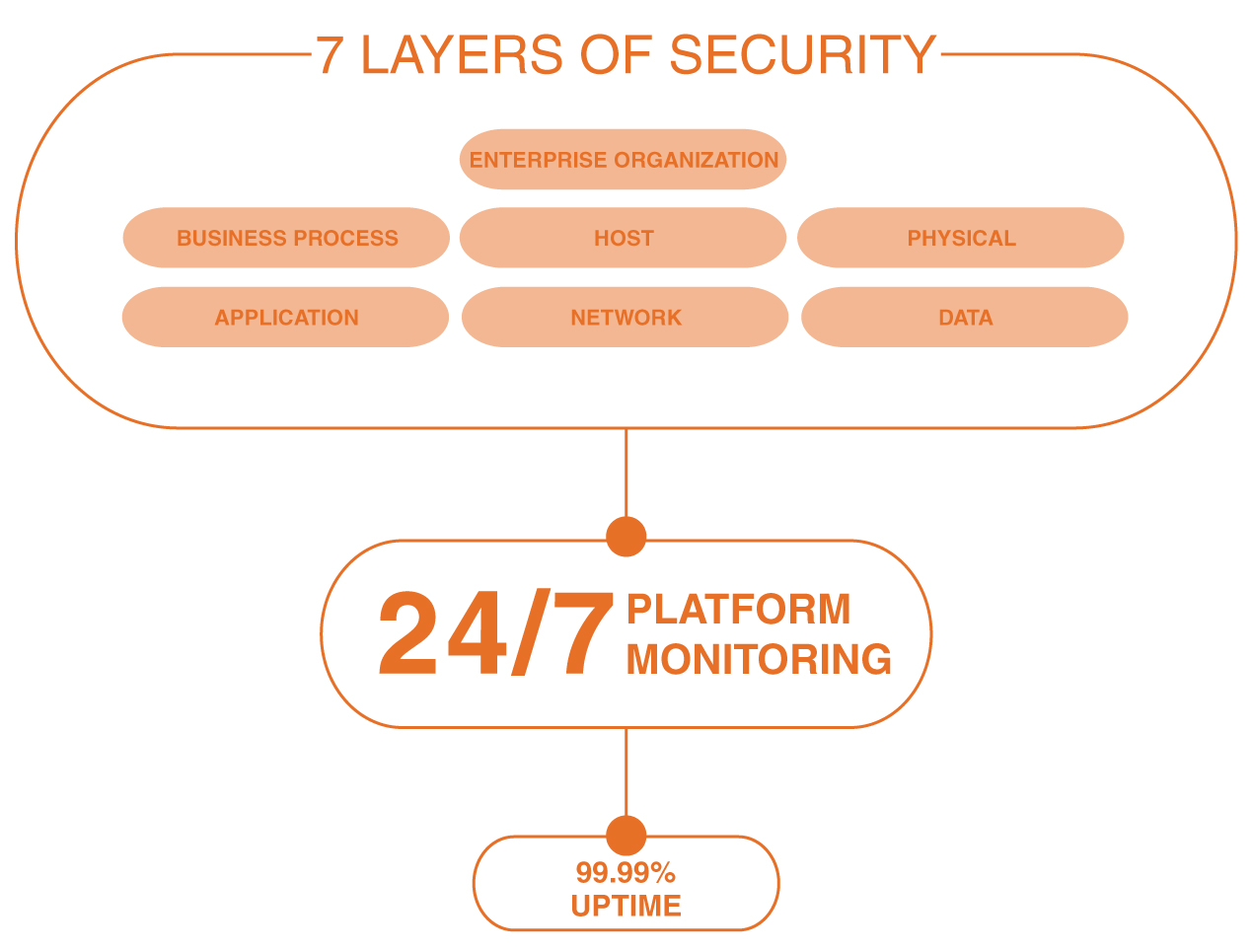
Clarity offers you added peace of mind by instituting robust security measures at every level for your architecture and processes. These include the physical, network, host, data, application, and business processes, as well as the enterprise level of your organization.
Clarity Voice.s UCaaS system ensures that customer calls and fax messages are secure with encryption in transit and at-rest, along with other features, protecting data and guarding against unauthorized access to protected health information.
BEST-IN-CLASS NETWORK SECURITY & RELIABILITY
Clarity makes it easy to run a fully secure business.

We Never Sleep
We maintain 24//365 coverage in our networking and user support center just in case you call.

No Power? No Problem
Redundant data center ensure seamless failover. If a natural disaster strikes, we have you covered coast to coast.

No Internet? No Problem
If an internet backbone issue occurs at your ISP, we’ll seamlessly transfer your calls to your mobile devices.

No Time for Downtime
Our reliable Networks with carrier-grade data centers, strive for 99.999% up-time, so you’ll never miss a beat with your customers.

Always Informed
Know our system status 24/7. You’ll know instantly if our performance is impacted by a carrier, network backbone, system maintenance or other issue at clarityvoice.com/support

Technically Certified Support
Get any problem solved fast with our technically certified USA based support team. You’ll always talk to a real human and get real answers, every time.
SECURITY & RELIABILITY ARE ALWAYS TOP PRIORITIES
We’ve made it easy to run a fully secure business.
Clarity makes it easy to run a fully secure business.

Monitoring 24/7
Our VoIP certified engineers watch our network at all times. With consistent monitoring, any network issues are immediately flagged and actively solved.

We Take Security Seriously
We’ve got you covered. HIPAA, FISMA High, FedRAMP, SOC 2 Type 2, SOC 3, ISO 27001, ISO 50001, ISO 14001, ISO9001

Seven Distinct Layers…
…of physical and data security between endpoints.
- Data securely stored
- Application layer security
- Endpoint security
- Network security
- Perimeter and other layers of physical security
- Policy management thru SOP’s
- Monitoring

Fax Document & Call Recordings
- All fax cashing is purged following successful transmission; aka we do not store any fax document.
- Call recordings can be set to be continual or on demand.
- All continual call recordin plans are auto purged at 30-days unless a long-term storage plan is purchased.
NEED TO KNOW EVEN MORE? WE GET YOU.
Let’s speak geek-to-geek if this doesn’t satisfy.
VOICE DATA
- Our Multiple Data Centers are designed to be compliant
- Data Center 1: HIPAA – PCI – FISMA High – FedRAMP – SOC2 Type 2 – SOC 3 – ISO 27001 – ISO 50001 – ISO 14001 – ISO 9001
- Data Center 2: HIPAA, PCI-DSS, and SSAE-18 SOC2 TypeII/SOC 3 compliant
- Data is stored securely (in the sense that we require authentication for access and access is provided only to those who need it to do their job)
- All systems are behind firewalls
- All Data is stored securely and behind a firewall
- Customer data that could provide ePHI are encrypted during all transmissions (voice is configurable)
- Encryption: All in and out data transport are secured through appropriate levels of encryption
- All passwords are encrypted and regularly request to be reset by users
- System access is restricted to only authorized users that maintain our systems
- Automatic log off features are implemented on all systems
- Recordings purged. Any customer choosing to use call recording functionality is set to purge automatically after 30-days and likewise access to these files are permission based at an individual user
- Seven distinct layers of physical and data security between endpoints
- Data securely stored
- Application layer security
- Endpoint security
- Network security
- Perimeter and other layers of physical security
- Policy management thru SOP’s
- Monitoring



